Android11编译第六弹:user版本增加su+内置root用户
问题1:user版本默认不开放root,adb登录后默认采用system用户,收紧用户权限;
问题2:因为有些功能需要用到root用户,例如设置网卡地址,网卡开启和关闭等,因为线上设备user版本没有root用户开放,很不方便。采用允许登录root用户的方式,登录时增加密码验证。
问题3:默认采用system用户以后,支持APK静默升级和OTA静默安装。
一、编译su命令
在AOSP的"user"版本中添加su功能是一个比较复杂的过程,因为"user"版本旨在提供更高的安全性和限制对系统的访问权限。默认情况下,AOSP的"user"版本不包含su功能。但是,您可以尝试以下方法来增加su功能:
-
编译AOSP源代码:设置并编译AOSP源代码,确保您已经正确设置了AOSP的开发环境,并可以成功编译"user"版本的AOSP。
-
修改SELinux策略:在"user"版本中,SELinux(安全增强型Linux)通常会限制对系统的访问权限。您需要修改SELinux策略,以允许su执行以及相关的特权操作。这涉及修改SELinux策略文件和规则,以便允许su二进制文件在"user"版本中运行。
-
添加su二进制文件:将su二进制文件添加到AOSP源代码树中的适当位置,例如/system/xbin/su。
-
设置su的权限和所有者:确保su二进制文件的权限和所有者设置正确。通常,su二进制文件的权限应设置为-rwsr-sr-x(4755),所有者应设置为root。
-
修改init.rc文件:编辑AOSP源代码树中的init.rc文件,以确保su二进制文件在系统启动时被执行。在init.rc文件中添加以下行:
service su /system/bin/su class main user root group root disabled这将在系统启动时启动su服务。
-
重新编译AOSP:运行适当的编译命令,重新编译"user"版本的AOSP源代码以包含您添加的su功能。具体的编译命令取决于您的AOSP版本和配置。
-
刷入编译后的系统镜像:将编译后的系统镜像刷入目标设备。根据您的设备和刷机工具,执行相应的操作来刷入系统镜像。
1.1 user版本也编译su
用户切换需要用到su指令。su指令对应的AOSP代码目录:
/system/extras/su
修改MakeFile文件Android.mk,增加一行:
#可以为user、eng、tests、optional,optional代表在任何版本下都编译 LOCAL_MODULE_TAGS := optional
在user版本也编译生成su程序。
1.2 配置user版本编译su
在build/target/product/base_system.mk,增加su编译
272 watchdogd \
273 wificond \
274 wifi.rc \
275 wm \
su \ --> add by zhouronghua
276
277 # VINTF data for system image
278 PRODUCT_PACKAGES += \
279 system_manifest.xml \
280 system_compatibility_matrix.xml \
在wm \ 后面增加 su , 即打包user版本的时候也编译su程序。
执行
$ make -j16
进行编译,编译以后,查找su文件的输出目录
$ find . -name "su"
root@ubuntu:/sandstar_aosp/LA.UM.9.14.1_MT564# find . -name "su"
./system/extras/su
./out/.path/su
得到输出文件在 out/.path/su
打包生成ROM以后,刷机完成.
1.3 su指令集成到ROM包
编译生成的su,需要集成到ROM包中
device/qcom/lahaina/lahaina.mk
# Fix: add by zhouronghua user version add su start PRODUCT_PACKAGES += su # user version add su end
因为在1.2已经配置打包到系统中,此步骤已经重复设置,不需要了。
在/system/xbin/下面存在su 二进制文件了。
lahaina:/ # cd /system system/ system_ext/ lahaina:/ # cd /system/xbin/ lahaina:/system/xbin # ls su lahaina:/system/xbin # ./su --help usage: su [WHO [COMMAND...]] Switch to WHO (default 'root') and run the given COMMAND (default sh). WHO is a comma-separated list of user, group, and supplementary groups in that order. lahaina:/system/xbin # ls -al su -rwsr-sr-x 1 root shell 11632 2009-01-01 08:00 su
1.4 设置su的权限和所有者
在system/core/libcutils/fs_config.cpp
// are NOT included on user builds.
{ 06755, AID_ROOT, AID_ROOT, 0, "system/xbin/procmem" },
// ==== modify begin ==== zhouronghua su right improve
{ 06755, AID_ROOT, AID_SHELL, 0, "system/xbin/su" },
// ==== modify end ====
// the following files have enhanced capabilities and ARE included
配置su指令的权限和所有者。
1.5 系统启动脚本su配置权限
system/core/rootdir/init.rc
chmod 0660 /sys/devices/system/cpu/cpufreq/interactive/io_is_busy
# ==== modify begin ==== zhouronghua su right
chmod 6755 /system/xbin/su
# ==== modify end ====
修改su的权限为6755
二、配置su SELinux策略
默认不需要开启ROOT权限。
/system/sepolicy/private/file_contexts
/system/xbin/su u:object_r:su_exec:s0
SeLinux即类型强制访问控制,包含四个部分
- 源类型(Source type(s) ) 通常是尝试访问的进程的域类型
- 目标类型(Target type(s) ) 被进程访问的客体的类型
- 客体类别(Object class(es)) 指定允许访问的客体的类型
- 许可(Permission(s))象征目标类型允许源类型访问客体类型的访问种类
su相关的SELinux策略。
对应su_exec 应该要运行执行程序su
4 domain_auto_trans(shell, su_exec, su) 7 domain_auto_trans(dumpstate, su_exec, su)
可以看到分配给shell程序和dumpstate程序访问su的策略为su_exec。
2.1 配置su SELinux策略全部编译版本生效
su的SELinux策略文件为
/system/sepolicy/public/su.te
/system/sepolicy/private/su.te
/system/sepolicy/public/su.te 5 # File types must be defined for file_contexts. 6 type su_exec, system_file_type, exec_type, file_type;
su_exec允许访问的客体类型,是系统文件类型,可执行文件类型,文件类型。
8 userdebug_or_eng(` 9 # Domain used for su processes, as well as for adbd and adb shell 10 # after performing an adb root command. The domain definition is 11 # wrapped to ensure that it does not exist at all on -user builds. 12 typeattribute su mlstrustedsubject; 13 14 # Add su to various domains 15 net_domain(su)
注意:默认的su进程,adbd或者adb shell, 执行adb root
这个功能在user版本的编译中不存在。
也就是默认user版本不会添加su 指令。因此,user版本添加su指令后,还需要在su版本添加
userdebug_or_eng这个方法是什么含义呢?
只有在userdebug和eng构建版本类型才会生效,user版本不会生效。相当于一个构建开关。
因为我们需要在user版本也开放su功能,因此需要去掉这个开关,使之所有版本都生效。
2.2 配置su_exec 访问SeLinux策略
其他程序访问su,需要配置SeLinux策略。
/system/sepolicy/public/domain.te
1106 # Nobody should be able to execute su on user builds.
1107 # On userdebug/eng builds, only dumpstate, shell, and
1108 # su itself execute su.
1109 neverallow { domain userdebug_or_eng(`-dumpstate -shell -su') } su_exec:file no_x_file_perms;
只有userdebug和eng构建版本中,dumpstate/shell/su三者执行su 指令,其他任何构建版本的其他程序都不允许执行su。
规则修改为:
所有版本构建中,dumpstate/shell/su三者执行su 指令,其他任何程序都不允许执行su。
neverallow { domain -dumpstate -shell -su } su_exec:file no_x_file_perms;
2.3 对应版本的API SELinux策略修改
system/sepolicy/public/domain.te对应的安卓11 SELinux策略文件。
对应的策略文件必须与system/sepolicy/public/domain.te完全相同。
cp system/sepolicy/public/domain.te system/sepolicy/prebuilts/api/30.0/public/domain.te
cp system/sepolicy/public/domain.te system/sepolicy/prebuilts/api/30.0/public/domain.te
同理,system/sepolicy/public/su.te对应安卓11的SELinux策略文件修改
cp system/sepolicy/public/su.te system/sepolicy/prebuilts/api/30.0/public/su.te
cp system/sepolicy/private/su.te system/sepolicy/prebuilts/api/30.0/private/su.te
cp system/sepolicy/public/su.te system/sepolicy/prebuilts/api/30.0/public/su.te cp system/sepolicy/private/su.te system/sepolicy/prebuilts/api/30.0/private/su.te
同样关闭userdebug_or_eng标签,保证所有的构建版本都添加su
同理,修改API版本29.0,28.0,27.0和26.0版本对应的策略文件。
修改后编译,错误日志信息:
root@ubuntu:/sandstar_aosp/LA.UM.9.14.1_MT564# out/target/product/qssi/obj/FAKE/sepolicy_neverallows_intermediates/sepolicy_neverallows
-bash: out/target/product/qssi/obj/FAKE/sepolicy_neverallows_intermediates/sepolicy_neverallows: No such file or directory
root@ubuntu:/sandstar_aosp/LA.UM.9.14.1_MT564# /bin/bash -c "(ASAN_OPTIONS=detect_leaks=0 out/host/linux-x86/bin/checkpolicy -M -c 30 -o out/target/product/qssi/obj/FAKE/sepolicy_neverallows_intermediates/sepolicy_neverallows.tmp out/target/product/qssi/obj/FAKE/sepolicy_neverallows_intermediates/policy.conf ) && (out/host/linux-x86/bin/sepolicy-analyze out/target/product/qssi/obj/FAKE/sepolicy_neverallows_intermediates/sepolicy_neverallows.tmp neverallow -w -f out/target/product/qssi/obj/FAKE/sepolicy_neverallows_intermediates/policy_2.conf || ( echo \"\" 1>&2; echo \"sepolicy-analyze failed. This is most likely due to the use\" 1>&2; echo \"of an expanded attribute in a neverallow assertion. Please fix\" 1>&2; echo \"the policy.\" 1>&2; exit 1 ) ) && (touch out/target/product/qssi/obj/FAKE/sepolicy_neverallows_intermediates/sepolicy_neverallows.tmp ) && (mv out/target/product/qssi/obj/FAKE/sepolicy_neverallows_intermediates/sepolicy_neverallows.tmp out/target/product/qssi/obj/FAKE/sepolicy_neverallows_intermediates/sepolicy_neverallows )"
libsepol.report_failure: neverallow on line 37 of system/sepolicy/private/app.te (or line 33603 of policy.conf) violated by allow su incident:process { transition };
libsepol.report_failure: neverallow on line 37 of system/sepolicy/private/app.te (or line 33603 of policy.conf) violated by allow su perfetto:process { transition };
libsepol.report_failure: neverallow on line 37 of system/sepolicy/private/app.te (or line 33603 of policy.conf) violated by allow su dumpstate:process { transition };
libsepol.report_failure: neverallow on line 1208 of system/sepolicy/public/domain.te (or line 13710 of policy.conf) violated by allow dumpstate su:process { transition };
libsepol.report_failure: neverallow on line 1208 of system/sepolicy/public/domain.te (or line 13710 of policy.conf) violated by allow shell su:process { transition };
libsepol.report_failure: neverallow on line 699 of system/sepolicy/public/domain.te (or line 12842 of policy.conf) violated by allow su vndservicemanager:binder { call transfer };
libsepol.report_failure: neverallow on line 681 of system/sepolicy/public/domain.te (or line 12811 of policy.conf) violated by allow su vndbinder_device:chr_file { ioctl read write getattr lock append map open watch watch_reads };
libsepol.check_assertions: 7 neverallow failures occurred
Error while expanding policy
root@ubuntu:/sandstar_aosp/LA.UM.9.14.1_MT564# vi libsepol.report_failure: neverallow on line 37 of system/sepolicy/private/app.te (or line 33603 of policy.conf) violated by allow su incident:process { transition };
-bash: syntax error near unexpected token `('
root@ubuntu:/sandstar_aosp/LA.UM.9.14.1_MT564# vi system/sepolicy/private/app.te
2.4 app.te配置su SELinux策略
system/sepolicy/private/app.te
# Transition to a non-app domain.
# Exception for the shell and su domains, can transition to runas, etc.
# Exception for crash_dump to allow for app crash reporting.
# Exception for renderscript binaries (/system/bin/bcc, /system/bin/ld.mc)
# to allow renderscript to create privileged executable files.
# ==== modify by zhouronghua all builds has su
#neverallow { appdomain -shell userdebug_or_eng(`-su') }
# { domain -appdomain -crash_dump -rs }:process { transition };
#neverallow { appdomain -shell userdebug_or_eng(`-su') }
# { domain -appdomain }:process { dyntransition };
neverallow { appdomain -shell -su }
{ domain -appdomain -crash_dump -rs }:process { transition };
neverallow { appdomain -shell -su }
{ domain -appdomain }:process { dyntransition };
# ==== modify by zhouronghua 2023/11/21
appdomain除了shell和su禁止使用
neverallow没有被allow到的动作默认就不允许执行的
2.5 domain.te配置zygote允许su
system/sepolicy/public/domain.te
# Only domains spawned from zygote, runas and simpleperf_app_runner may have
# the appdomain attribute. simpleperf is excluded as a domain transitioned to
# when running an app-scoped profiling session.
# ==== modify by zhouronghua all builds has su
#neverallow { domain -simpleperf_app_runner -runas -app_zygote -webview_zygote -zygote } {
# appdomain -shell -simpleperf userdebug_or_eng(`-su')
#}:process { transition dyntransition };
neverallow { domain -simpleperf_app_runner -runas -app_zygote -webview_zygote -zygote } {
appdomain -shell -simpleperf -su
}:process { transition dyntransition };
# ==== modify by zhouronghua 2023/11/21
2.6 zygote增加su 策略
system/sepolicy/private/app_zygote.te
# Only allow app_zygote to talk to the logd socket, and
# su/heapprofd/traced_perf on eng/userdebug. This is because
# cap_setuid/cap_setgid allow to forge uid/gid in SCM_CREDENTIALS.
# Think twice before changing.
# ==== modify by zhouronghua all builds has su
neverallow app_zygote {
domain
-app_zygote
-logd
-system_server
-su
userdebug_or_eng(`-heapprofd')
userdebug_or_eng(`-traced_perf')
}:unix_dgram_socket *;
neverallow app_zygote {
domain
-app_zygote
-su
userdebug_or_eng(`-heapprofd')
userdebug_or_eng(`-traced_perf')
}:unix_stream_socket *;
# ==== modify by zhouronghua 2023/11/21
修改完成同步到API版本
cp system/sepolicy/private/app_zygote.te system/sepolicy/prebuilts/api/30.0/private/app_zygote.te
2.7 adbd配置su 策略
system/sepolicy/private/adbd.te
# No transitions from adbd to non-shell, non-crash_dump domains. adbd only ever
# transitions to the shell domain (except when it crashes). In particular, we
# never want to see a transition from adbd to su (aka "adb root")
neverallow adbd { domain -crash_dump -shell }:process transition;
# ==== modify by zhouronghua all builds has su
#neverallow adbd { domain userdebug_or_eng(`-su') recovery_only(`-shell') }:process dyntransition;
neverallow adbd { domain -su recovery_only(`-shell') }:process dyntransition;
# ==== modify by zhouronghua 2023/11/21
修改完成同步到API
cp system/sepolicy/private/adbd.te system/sepolicy/prebuilts/api/30.0/private/adbd.te
2.8 logd增加su策略
system/sepolicy/private/logd.te
# protect the event-log-tags file
neverallow {
domain
-appdomain # covered below
-bootstat
-dumpstate
-init
-logd
userdebug_or_eng(`-logpersist')
-servicemanager
-system_server
-surfaceflinger
-zygote
} runtime_event_log_tags_file:file no_rw_file_perms;
# ==== modify by zhouronghua all builds has su
neverallow {
appdomain
-bluetooth
-platform_app
-priv_app
-radio
-shell
-su
-system_app
} runtime_event_log_tags_file:file no_rw_file_perms;
# ==== modify by zhouronghua 2023/11/21
同步到API
cp system/sepolicy/private/logd.te system/sepolicy/prebuilts/api/30.0/private/logd.te
2.9 hal_configstore.tehal_configstore.te添加su策略hal_configstore.te
system/sepolicy/public/hal_configstore.te
# Should never need network access. Disallow sockets except for
# for unix stream/dgram sockets used for logging/debugging.
neverallow hal_configstore_server domain:{
rawip_socket tcp_socket udp_socket
netlink_route_socket netlink_selinux_socket
socket netlink_socket packet_socket key_socket appletalk_socket
netlink_tcpdiag_socket netlink_nflog_socket
netlink_xfrm_socket netlink_audit_socket
netlink_dnrt_socket netlink_kobject_uevent_socket tun_socket
netlink_iscsi_socket netlink_fib_lookup_socket netlink_connector_socket
netlink_netfilter_socket netlink_generic_socket netlink_scsitransport_socket
netlink_rdma_socket netlink_crypto_socket
} *;
# ==== modify by zhouronghua all builds has su
neverallow hal_configstore_server {
domain
-hal_configstore_server
-logd
-su
-tombstoned
userdebug_or_eng(`-heapprofd')
userdebug_or_eng(`-traced_perf')
}:{ unix_dgram_socket unix_stream_socket } *;
# ==== modify by zhouronghua 2023/11/21
cp system/sepolicy/public/hal_configstore.te system/sepolicy/prebuilts/api/30.0/public/hal_configstore.te
同步到API版本
2.10 cameraserver.te添加su策略
system/sepolicy/public/cameraserver.te
# Allow shell commands from ADB for CTS testing/dumping
# ==== modify by zhouronghua all builds has su
#userdebug_or_eng(`
allow cameraserver su:fd use;
allow cameraserver su:fifo_file { read write };
allow cameraserver su:unix_stream_socket { read write };
#')
# ==== modify by zhouronghua 2023/11/21
修改同步到API版本
cp system/sepolicy/public/cameraserver.te system/sepolicy/prebuilts/api/30.0/public/cameraserver.te
2.11 SE策略宏定义
system/sepolicy/public/te_macros
#####################################
# Build-time-only test
# SELinux rules which are verified during build, but not as part of *TS testing.
#
define(`build_test_only', ifelse(target_exclude_build_test, `true', , ))
####################################
# Fallback crash handling for processes that can't exec crash_dump (e.g. because of seccomp).
#
define(`crash_dump_fallback', `
# ==== modify by zhouronghua all builds has su
#userdebug_or_eng(`
allow su:fifo_file append;
#')
# ==== modify by zhouronghua 2023/11/21
allow anr_data_file:file append;
allow dumpstate:fd use;
allow incidentd:fd use;
# TODO: Figure out why write is needed.
allow dumpstate:fifo_file { append write };
allow incidentd:fifo_file { append write };
allow system_server:fifo_file { append write };
allow tombstoned:unix_stream_socket connectto;
allow tombstoned:fd use;
allow tombstoned_crash_socket:sock_file write;
allow tombstone_data_file:file append;
')
##################################### # pdx_service_socket_types(service, endpoint_dir_t) # Define types for endpoint and channel sockets. define(`pdx_service_socket_types', ` typeattribute pdx__endpoint_dir_type; type pdx__endpoint_socket, pdx__endpoint_socket_type, pdx_endpoint_socket_type, file_type, coredomain_socket, mlstrustedobject, mlstrustedsubject; type pdx__channel_socket, pdx__channel_socket_type, pdx_channel_socket_type, coredomain_socket; # ==== modify by zhouronghua all builds has su #userdebug_or_eng(` dontaudit su pdx__endpoint_socket:unix_stream_socket *; dontaudit su pdx__channel_socket:unix_stream_socket *; #') # ==== modify by zhouronghua 2023/11/21 ')
cp system/sepolicy/public/te_macros system/sepolicy/prebuilts/api/30.0/public/te_macros
2.12 statsd.te增加su策略
system/sepolicy/public/statsd.te
# Allow executing files on system, such as running a shell or running:
# /system/bin/toolbox
# /system/bin/logcat
# /system/bin/dumpsys
allow statsd devpts:chr_file { getattr ioctl read write };
allow statsd shell_exec:file rx_file_perms;
allow statsd system_file:file execute_no_trans;
allow statsd toolbox_exec:file rx_file_perms;
# ==== modify by zhouronghua all builds has su
#userdebug_or_eng(`
allow statsd su:fifo_file read;
#')
# ==== modify by zhouronghua 2023/11/21
cp system/sepolicy/public/statsd.te system/sepolicy/prebuilts/api/30.0/public/statsd.te
同步拷贝到API版本
2.13 iorapd.te增加su策略
system/sepolicy/public/iorapd.te
# Only system_server and shell (for dumpsys) can interact with iorapd over binder
neverallow { domain -dumpstate -system_server -iorapd } iorapd_service:service_manager find;
# ==== modify by zhouronghua all builds has su
neverallow iorapd {
domain
-healthd
-servicemanager
-system_server
-su
}:binder call;
cp system/sepolicy/public/iorapd.te system/sepolicy/prebuilts/api/30.0/public/iorapd.te
同步到API版本中
2.14 property.te增加su策略
system/sepolicy/public/property.te
# Don't audit legacy ctl. property handling. We only want the newer permission check to appear
# in the audit log
dontaudit domain {
ctl_bootanim_prop
ctl_bugreport_prop
ctl_console_prop
ctl_default_prop
ctl_dumpstate_prop
ctl_fuse_prop
ctl_mdnsd_prop
ctl_rildaemon_prop
}:property_service set;
neverallow {
domain
-init
} init_svc_debug_prop:property_service set;
# ==== modify by zhouronghua all builds has su
neverallow {
domain
-init
-dumpstate
-su
} init_svc_debug_prop:file no_rw_file_perms;
# ==== modify by zhouronghua 2023/11/21
同步到API版本中
cp system/sepolicy/public/property.te system/sepolicy/prebuilts/api/30.0/public/property.te
2.15 网络策略
system/sepolicy/public/netd.te
# apps may not interact with netd over binder.
neverallow { appdomain -network_stack } netd:binder call;
# ==== modify by zhouronghua all builds has su
#neverallow netd { appdomain -network_stack userdebug_or_eng(`-su') }:binder call;
neverallow netd { appdomain -network_stack -su }:binder call;
# ==== modify by zhouronghua 2023/11/21
同步到API
cp system/sepolicy/public/netd.te system/sepolicy/prebuilts/api/30.0/public/netd.te
2.16 安装增加su策略
system/sepolicy/public/installd.te
# only system_server, installd, dumpstate, and servicemanager may interact with installd over binder
neverallow { domain -system_server -dumpstate -installd } installd_service:service_manager find;
neverallow { domain -system_server -dumpstate -servicemanager } installd:binder call;
# ==== modify by zhouronghua all builds has su
neverallow installd {
domain
-system_server
-servicemanager
-su
}:binder call;
# ==== modify by zhouronghua 2023/11/21
userdebug_or_eng(`-su')替换为-su
然后同步API
cp system/sepolicy/public/installd.te system/sepolicy/prebuilts/api/30.0/public/installd.te
2.17 vold.te增加su策略
system/sepolicy/public/vold.te
neverallow {
domain
-system_server
-vdc
-vold
-update_verifier
-apexd
} vold_service:service_manager find;
# ==== modify by zhouronghua all builds has su
neverallow vold {
domain
-hal_health_storage_server
-hal_keymaster_server
-system_suspend_server
-hal_bootctl_server
-healthd
-hwservicemanager
-iorapd_service
-servicemanager
-system_server
-su
}:binder call;
# ==== modify by zhouronghua 2023/11/21
neverallow vold fsck_exec:file execute_no_trans;
neverallow { domain -init } vold:process { transition dyntransition };
neverallow vold *:process ptrace;
neverallow vold *:rawip_socket *;
同步修改到API
cp system/sepolicy/public/vold.te system/sepolicy/prebuilts/api/30.0/public/vold.te
2.18 user版本允许编译
改完后继续编译,再次出现新错误,user 版本不允许 permissive domains
# ==== modify by zhouronghua all builds has su
$(LOCAL_BUILT_MODULE): PRIVATE_CIL_FILES := $(all_cil_files)
$(LOCAL_BUILT_MODULE): PRIVATE_NEVERALLOW_ARG := $(NEVERALLOW_ARG)
$(LOCAL_BUILT_MODULE): $(HOST_OUT_EXECUTABLES)/secilc $(HOST_OUT_EXECUTABLES)/sepolicy-analyze $(all_cil_files) \
$(built_sepolicy_neverallows)
@mkdir -p $(dir $@)
$(hide) $ $@.permissivedomains
$(hide) if [ "$(TARGET_BUILD_VARIANT)" = "user" -a -s $@.permissivedomains ]; then \
echo "==========" 1>&2; \
echo "ERROR: permissive domains not allowed in user builds" 1>&2; \
echo "List of invalid domains:" 1>&2; \
cat $@.permissivedomains 1>&2; \
# exit 1; \
fi
$(hide) mv $@.tmp $@
# ==== modify by zhouronghua 2023/11/21
# ==== modify by zhouronghua all builds has su
$(LOCAL_BUILT_MODULE): $(sepolicy.recovery.conf) $(HOST_OUT_EXECUTABLES)/checkpolicy \
$(HOST_OUT_EXECUTABLES)/sepolicy-analyze
@mkdir -p $(dir $@)
$(hide) $(CHECKPOLICY_ASAN_OPTIONS) $(HOST_OUT_EXECUTABLES)/checkpolicy -M -c \
$(POLICYVERS) -o $@.tmp $ $@.permissivedomains
$(hide) if [ "$(TARGET_BUILD_VARIANT)" = "user" -a -s $@.permissivedomains ]; then \
echo "==========" 1>&2; \
echo "ERROR: permissive domains not allowed in user builds" 1>&2; \
echo "List of invalid domains:" 1>&2; \
cat $@.permissivedomains 1>&2; \
# exit 1; \
fi
$(hide) mv $@.tmp $@
# ==== modify by zhouronghua 2023/11/21
再次编译,已经通过。
三、关闭adb登录默认root权限
3.1 关闭adb root用户登录
原来默认adb进入后开启了root,当前需要关闭root
build/make/core/main.mk
ro.secure=0 恢复为ro.secure=1,默认不开启root登录
# ==== modify begin ====
# fix: zhouronghua default as root-->change to default
# Target is secure in user builds.
ADDITIONAL_DEFAULT_PROPERTIES += ro.secure=1
# ==== modify end ====
ADDITIONAL_DEFAULT_PROPERTIES += security.perf_harden=1
ifeq ($(user_variant),user)
# ==== modify begin ==== fix: default as root-->change to default
ADDITIONAL_DEFAULT_PROPERTIES += ro.adb.secure=1
# ==== modify end ====
endif
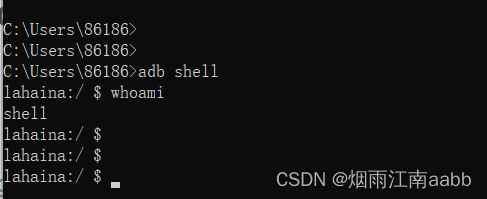
adb访问的时候,默认是shell,不能使用root超级权限。
3.2 ROM包验证是否切换shell用户
刷机以后,通过adb查看
可以看到默认不是root用户了,命令行也不是root用户的"#"号标记。
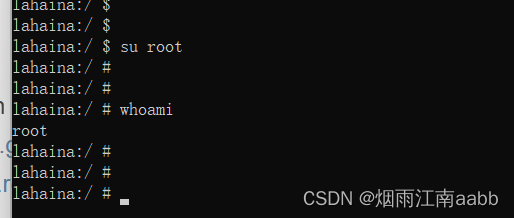
3.3 adb切换root用户登录
执行su root切换root用户试试
su root
四、确认默认静默升级是否受影响
静默升级安装调用的是系统的SystemUpdateSample,因为这个系统APP的权限没有改变,
静默升级安装应该不受影响。
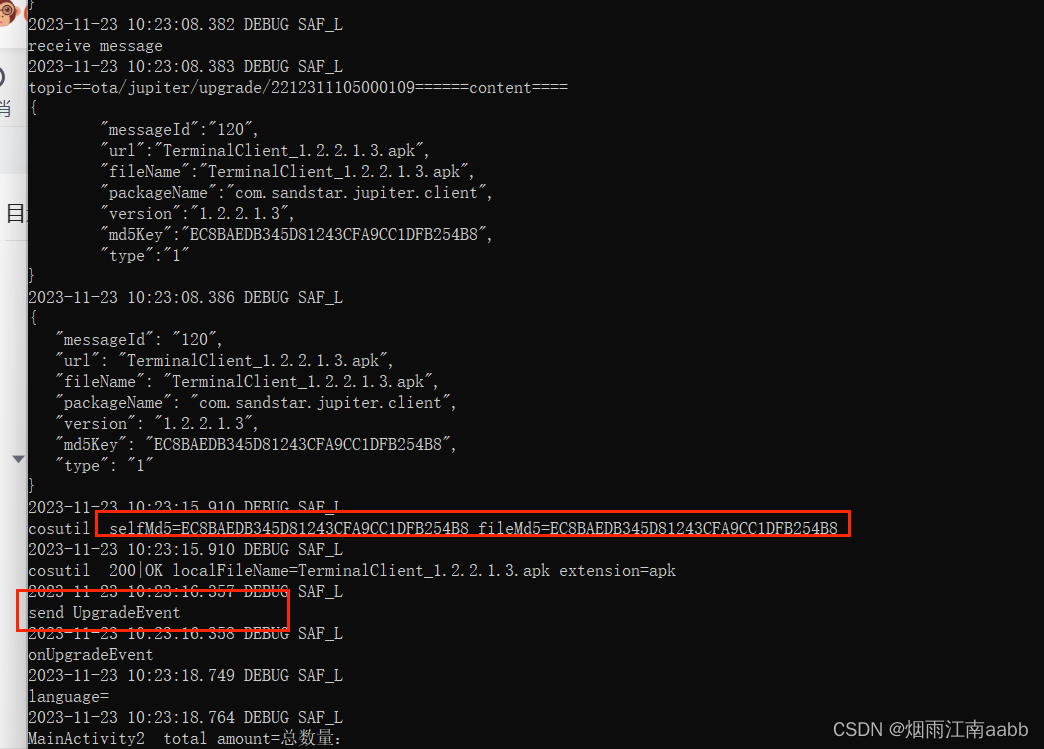
MQTT推送设备升级指令:
Topic: ota/jupiter/upgrade/2212311105000109QoS: 0
{
"messageId":"120",
"url":"TerminalClient_1.2.2.1.3.apk",
"fileName":"TerminalClient_1.2.2.1.3.apk",
"packageName":"com.sandstar.jupiter.client",
"version":"1.2.2.1.3",
"md5Key":"EC8BAEDB345D81243CFA9CC1DFB254B8",
"type":"1"
}
看日志下载安装成功
查询升级后的APP版本,确认已经升级到指定版本,静默安装成功。
五、内置root账户密码
????待进一步研究怎么弄。
For example in https://android.googlesource.com/device/google/marlin/+/refs/heads/android10-mainline-a-release/init.common.rc :
service vendor.power_sh /vendor/bin/init.power.sh
class main
user root
group root system
disabled
oneshot
on property:sys.boot_completed=1
start vendor.power_sh
Service定义语法:
service [ ]*
service名称
可执行文件路径
运行参数
约束选项,下文有讲解
选项讲解:
class [ \* ],声明service的类名,用来给service归类,所有在同一类名下的service可以被同时开启/终止。默认类名是'default'。 例如可以将开机过程中的动画service归入'amination'类。
user , 在执行该service前,切换用户为,默认是root。
group [ \* ],同上,切换group。
disabled,表明service不会自动启动,必须显式地通过名字来启动。
oneshot,当init进程结束时,不重启servicetianjitian'ji