第33关 使用gin开发webhook转发服务,实现prometheus和falco的钉钉、企业微信、飞书报警发送
------> 课程视频同步分享在今日头条和B站
大家好,我是博哥爱运维。
出这期视频,也是为了给第30关的falco公开课补一个坑,关于falco报警这块这期将补上,同时,对于这个gin开发的webhook服务源码这块,计划是放在后面运维golang开发课程里面再分享出来会比较好,毕竟这个需要一些golang开发语言的基础。
支持的镜像,为了方便大家下载使用,特地在阿里云注册一个个人镜像仓库:
registry.cn-beijing.aliyuncs.com/bogeit/boge-webhook:1.0
docker容器化运行
docker run -d \ --name boge-webhook \ -p 9999:9999 \ -e TZ="Asia/Shanghai" \ registry.cn-beijing.aliyuncs.com/bogeit/boge-webhook:1.0 \ -webhook https://open.feishu.cn/open-apis/bot/v2/hook/xxxxxxxxxxxxxxxxxxx \ -port 9999 \ -filters "serviceA,DeadMansSnitch"
k8s运行
apiVersion: v1
kind: Service
metadata:
name: boge-webhook
labels:
app: boge-webhook
model: falco
spec:
ports:
- port: 80
protocol: TCP
targetPort: 9999
type: ClusterIP
selector:
app: boge-webhook
model: falco
---
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: boge-webhook
model: falco
name: boge-webhook
spec:
replicas: 1
selector:
matchLabels:
app: boge-webhook
model: falco
template:
metadata:
labels:
app: boge-webhook
model: falco
spec:
containers:
- name: boge-webhook
image: registry.cn-beijing.aliyuncs.com/bogeit/boge-webhook:1.0
env:
- name: TZ
value: Asia/Shanghai
ports:
- containerPort: 9999
args:
- -webhook
- "https://open.feishu.cn/open-apis/bot/v2/hook/xxxxxxxxxxxxxxxxxxx"
- -port
- "9999"
- -filters
- "serviceA,DeadMansSnitch"
# 对于falco,filters白名单字段只填pod名称开头关键词是匹配所有ns,填namespace_pod开头关键词是匹配指定ns里面的服务
测试接口
# curl 10.0.1.201:9999/status
{"msg":"ok"}
# curl -X POST -H 'Content-type: application/json' -d '{"name": "boge","titlea": "'"$(id)"'", "texta": "'"$(whoami)--$(hostname)"'"}' 10.0.1.201:9999/b01bdc063/boge/getjson
# 查看webhook后端服务日志
# docker logs boge-webhook
[GIN-debug] [WARNING] Creating an Engine instance with the Logger and Recovery middleware already attached.
[GIN-debug] [WARNING] Running in "debug" mode. Switch to "release" mode in production.
- using env: export GIN_MODE=release
- using code: gin.SetMode(gin.ReleaseMode)
[GIN-debug] GET /status --> main.MyWebServer.func1 (3 handlers)
[GIN-debug] POST /b01bdc063/boge/getjson --> main.MyWebServer.func2 (3 handlers)
[GIN-debug] POST /7332f19/prometheus/dingtalk --> main.MyWebServer.func3 (3 handlers)
[GIN-debug] POST /1bdc0637/prometheus/feishu --> main.MyWebServer.func4 (3 handlers)
[GIN-debug] POST /5e00fc1a/prometheus/weixin --> main.MyWebServer.func5 (3 handlers)
[GIN-debug] POST /3c1e8/falcon/feishu --> main.MyWebServer.func6 (3 handlers)
[GIN-debug] POST /3c1e8/falcon/dingtalk --> main.MyWebServer.func7 (3 handlers)
[GIN-debug] POST /3c1e8/falcon/weixin --> main.MyWebServer.func8 (3 handlers)
[GIN-debug] [WARNING] You trusted all proxies, this is NOT safe. We recommend you to set a value.
Please check https://pkg.go.dev/github.com/gin-gonic/gin#readme-don-t-trust-all-proxies for details.
[GIN-debug] Listening and serving HTTP on :9999
{"name": "boge","titlea": "uid=0(root) gid=0(root) groups=0(root)", "texta": "root--boge"}
[GIN] 2024/04/02 - 17:45:50 | 200 | 78.745µs | 10.0.1.201 | POST "/b01bdc063/boge/getjson"
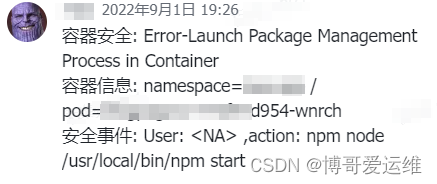
编辑 falco 服务的 webhook 接收配置
falco相关内容可以查看博哥之前分享的文档: https://blog.csdn.net/weixin_46887489/article/details/135758197 # 配置 falcosidekick 报警输出的 webhook 地址: kubectl -n falco edit secrets falco-falcosidekick #在下面配置(内容是base64编码 http://10.0.1.201:9999/3c1e8/falcon/feishu) WEBHOOK_ADDRESS: aaHR0cDovLzEwLjAuMS4yMDE6OTk5OS8zYzFlOC9mYWxjb24vZmVpc2h1Cg==
编辑 prometheus 服务的 webhook 接收配置
http://10.0.1.201:9999/1bdc0637/prometheus/feishu 详细配置见博哥之前讲解的 prometheus发送报警的文档: https://blog.csdn.net/weixin_46887489/article/details/135612462
大家有什么问题,可以找博哥进技术交流群里面交流,目前群已接近400人,想进群趁早
免责声明:我们致力于保护作者版权,注重分享,被刊用文章因无法核实真实出处,未能及时与作者取得联系,或有版权异议的,请联系管理员,我们会立即处理!
部分文章是来自自研大数据AI进行生成,内容摘自(百度百科,百度知道,头条百科,中国民法典,刑法,牛津词典,新华词典,汉语词典,国家院校,科普平台)等数据,内容仅供学习参考,不准确地方联系删除处理!
图片声明:本站部分配图来自人工智能系统AI生成,觅知网授权图片,PxHere摄影无版权图库和百度,360,搜狗等多加搜索引擎自动关键词搜索配图,如有侵权的图片,请第一时间联系我们,邮箱:ciyunidc@ciyunshuju.com。本站只作为美观性配图使用,无任何非法侵犯第三方意图,一切解释权归图片著作权方,本站不承担任何责任。如有恶意碰瓷者,必当奉陪到底严惩不贷!