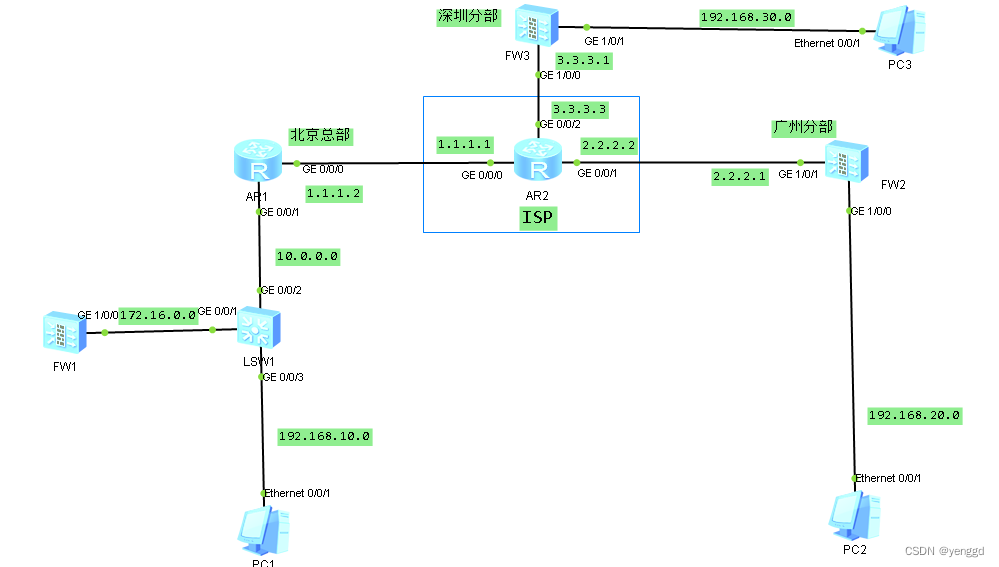
华为防火墙总部加多分部ipsec-*** nat穿越,***核心旁挂式组网案例命令行和web配置
实现效果:
1、总部和各分部固定IP的ipsec ***连接,网段192.168.10.0至192.168.20.0、192.168.30.0都能互相进行互相访问,并且都还能上互联网。 总部***设备在核心交换机上旁挂,并且做nat穿越出口路由器。
2、 分部之间相互访问是经过总部的***绕行
总部AR1出口路由器配置:
dis current-configuration
[V200R003C00]
acl number 3000
rule 5 deny ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
//先把***的网段拿 掉
rule 10 deny ip source 192.168.10.0 0.0.0.255 destination 192.168.30.0 0.0.0.255
//先把***的网段拿 掉
rule 15 permit ip source 192.168.10.0 0.0.0.255 //上外网
rule 20 permit ip source 172.16.0.0 0.0.0.255 //上外网,必须保证***主机能访问公网
interface GigabitEthernet0/0/0 //放行udp 500 4500两个*** 穿越端口
ip address 1.1.1.2 255.255.255.0
nat server protocol udp global current-interface 4500 inside 172.16.0.2 4500
nat server protocol udp global current-interface 500 inside 172.16.0.2 500
nat outbound 3000
interface GigabitEthernet0/0/1
ip address 10.0.0.1 255.255.255.0
ip route-static 0.0.0.0 0.0.0.0 1.1.1.1
ip route-static 172.16.0.0 255.255.255.0 10.0.0.2
ip route-static 192.168.10.0 255.255.255.0 10.0.0.2
总部核心交换机配置:
dhcp enable
interface Vlanif10
ip address 192.168.10.1 255.255.255.0
dhcp select interface
interface Vlanif100
ip address 172.16.0.1 255.255.255.0
interface Vlanif999
ip address 10.0.0.2 255.255.255.0
interface MEth0/0/1
interface GigabitEthernet0/0/1
port link-type access
port default vlan 100
interface GigabitEthernet0/0/2
port link-type access
port default vlan 999
interface GigabitEthernet0/0/3
port link-type access
port default vlan 10
ip route-static 192.168.30.0 255.255.255.0 172.16.0.2 //把内网访问***的网段引给***
ip route-static 0.0.0.0 0.0.0.0 10.0.0.1 //上外网
ip route-static 192.168.20.0 255.255.255.0 172.16.0.2 //把内网访问***的网段引给***
3台防火墙策略全部放行不做限制
总部FW1配置:
acl number 3000
rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
rule 10 permit ip source 192.168.30.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
acl number 3001
rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.30.0 0.0.0.255
rule 10 permit ip source 192.168.20.0 0.0.0.255 destination 192.168.30.0 0.0.0.255
ipsec proposal prop27111711204
encapsulation-mode auto
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ipsec proposal prop28111045368
encapsulation-mode auto
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 2
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike peer ike271117112046
exchange-mode auto
pre-shared-key adminadmin
ike-proposal 1
remote-id-type ip
remote-id 2.2.2.1
local-id 1.1.1.2
dpd type periodic
remote-address 2.2.2.1
ike peer ike281110453684
exchange-mode auto
pre-shared-key adminadmin
ike-proposal 2
remote-id-type ip
remote-id 3.3.3.1
local-id 1.1.1.2
dpd type periodic
remote-address 3.3.3.1
ipsec policy ipsec2711171120 1 isakmp
security acl 3000
ike-peer ike271117112046
proposal prop27111711204
tunnel local applied-interface
alias to-gz
sa trigger-mode auto
sa duration traffic-based 10485760
sa duration time-based 3600
ipsec policy ipsec2711171120 2 isakmp
security acl 3001
ike-peer ike281110453684
proposal prop28111045368
tunnel local applied-interface
alias to-sz
sa trigger-mode auto
sa duration traffic-based 10485760
sa duration time-based 3600
interface GigabitEthernet1/0/0
undo shutdown
ip address 172.16.0.2 255.255.255.0
service-manage ping permit
ipsec policy ipsec2711171120
firewall zone local
set priority 100
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
firewall zone untrust
set priority 5
firewall zone dmz
set priority 50
ip route-static 0.0.0.0 0.0.0.0 172.16.0.1
ip route-static 192.168.10.0 255.255.255.0 172.16.0.1
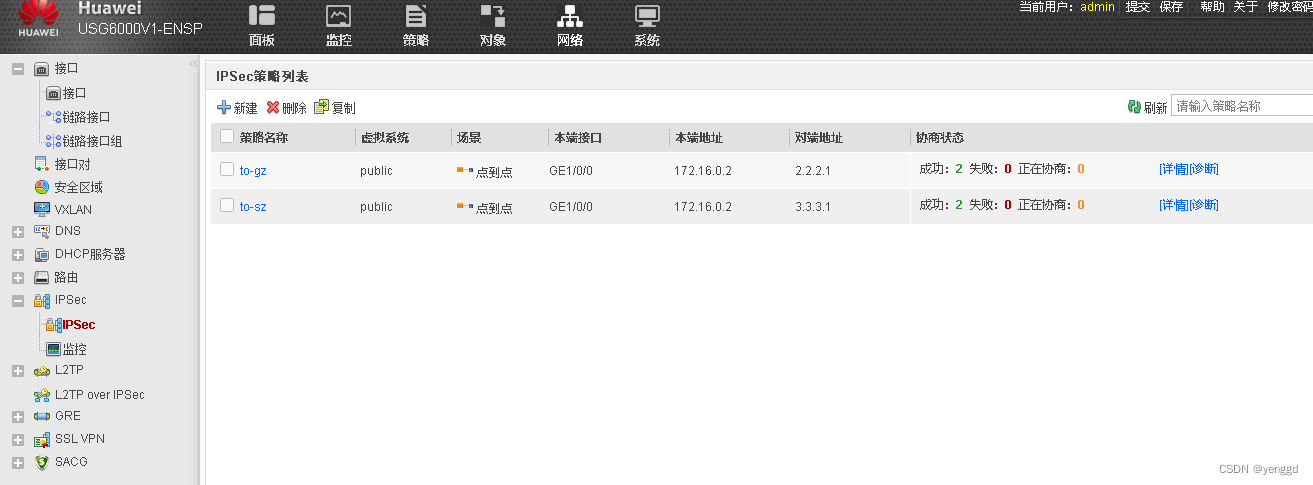
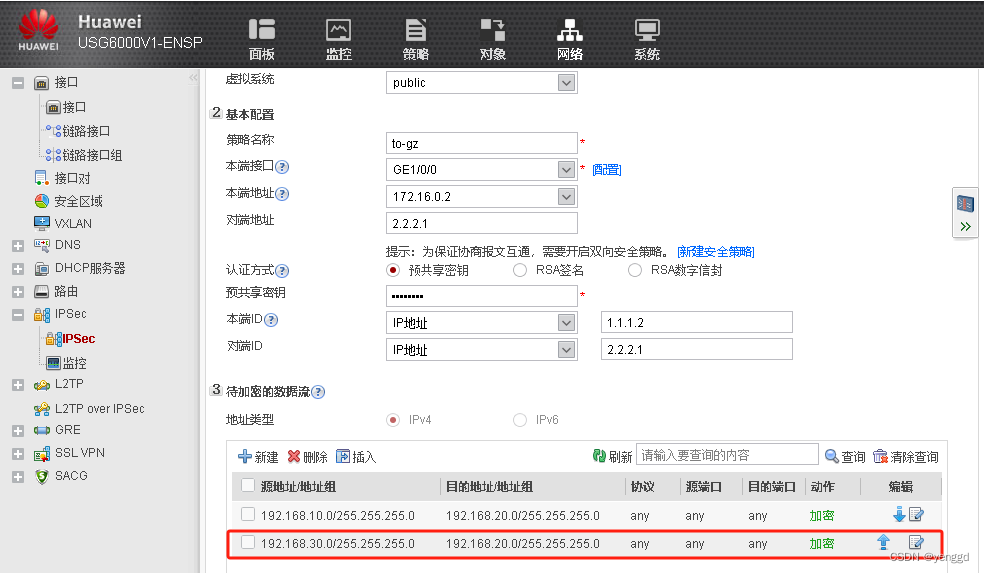
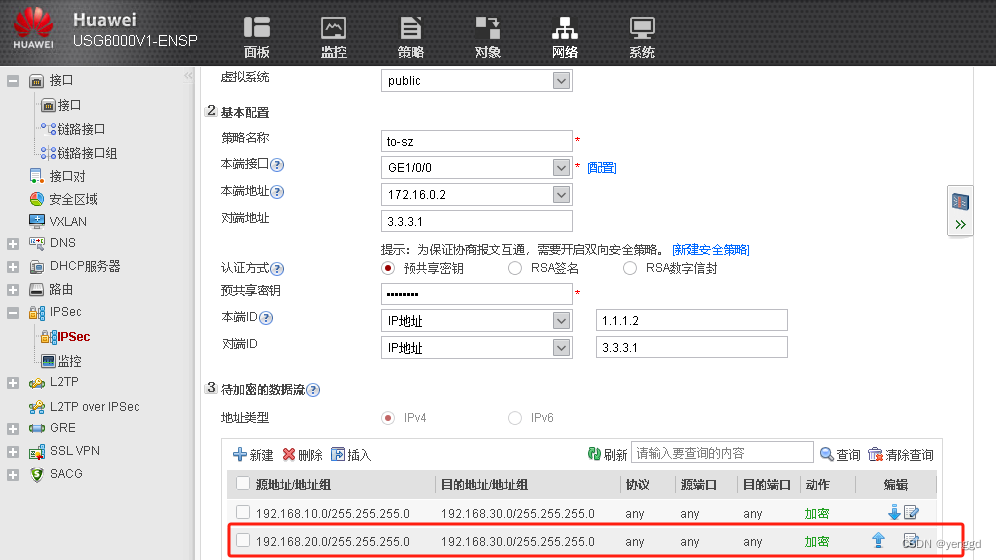
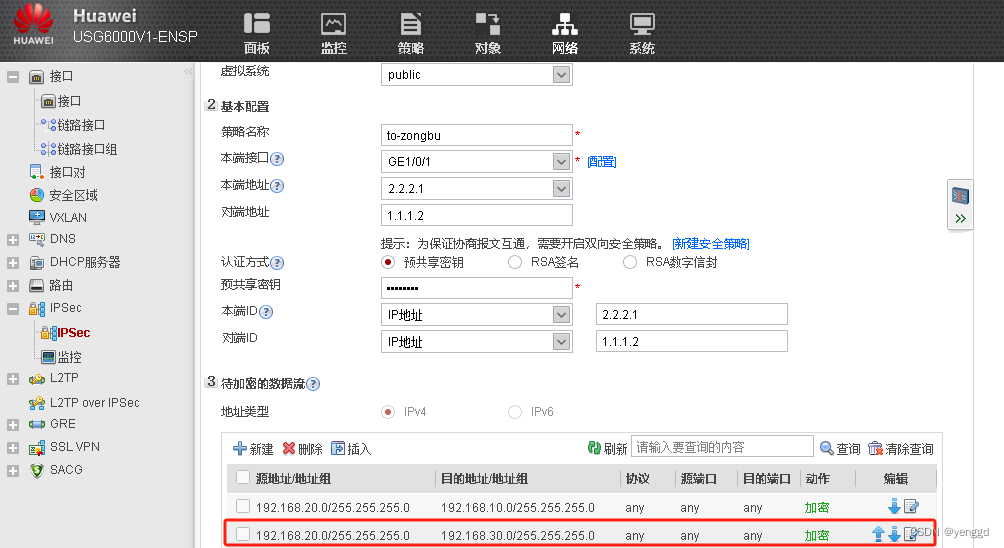
FW1的 WEB配置:
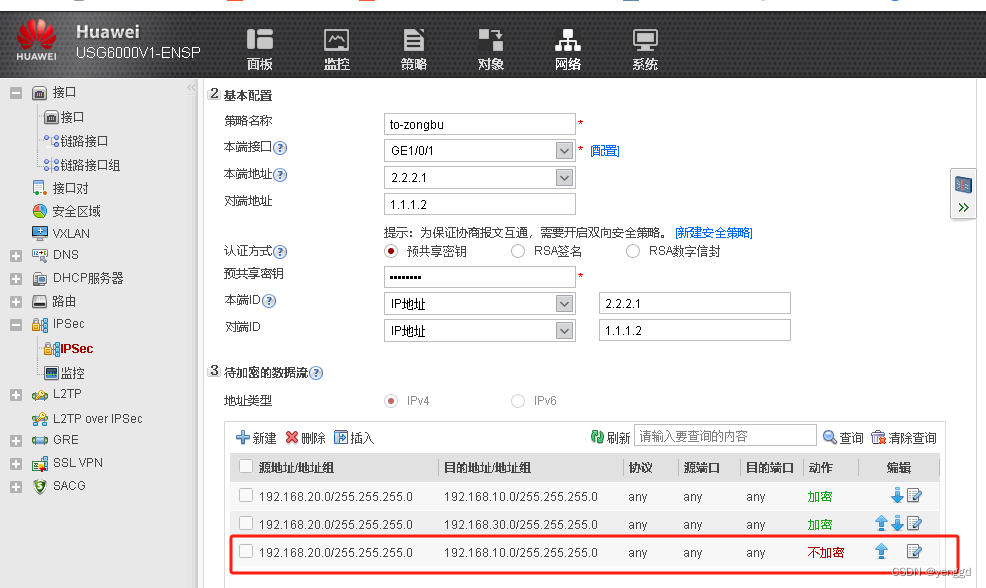
2条一个去sz,一个去gz
保证两个分部可以通过总部节点通,要加上这条网段,两条***都得加:
FW2的配置:
acl number 3000
rule 5 permit ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
rule 10 permit ip source 192.168.20.0 0.0.0.255 destination 192.168.30.0 0.0.0.255
rule 15 deny ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
ipsec proposal prop27111785448
encapsulation-mode auto
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike peer ike271117854480
exchange-mode auto
pre-shared-key adminadmin
ike-proposal 1
remote-id-type ip
remote-id 1.1.1.2
local-id 2.2.2.1
dpd type periodic
remote-address 1.1.1.2
ipsec policy ipsec2711178542 1 isakmp
security acl 3000
ike-peer ike271117854480
proposal prop27111785448
tunnel local applied-interface
alias to-zongbu
sa trigger-mode auto
sa duration traffic-based 10485760
sa duration time-based 3600
interface GigabitEthernet1/0/0
undo shutdown
ip address 192.168.20.1 255.255.255.0
dhcp select interface
interface GigabitEthernet1/0/1
undo shutdown
ip address 2.2.2.1 255.255.255.0
service-manage ping permit
ipsec policy ipsec2711178542
interface GigabitEthernet1/0/6
undo shutdown
firewall zone local
set priority 100
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
firewall zone dmz
set priority 50
ip route-static 0.0.0.0 0.0.0.0 2.2.2.2
security-policy
default action permit
policy-based-route
nat-policy
rule name ***
source-zone trust
destination-zone untrust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.30.0 mask 255.255.255.0
action no-nat
rule name internet
source-zone trust
destination-zone untrust
action source-nat easy-ip
FW2的WEB配置:
最后一条要手动添加去往sz的网段
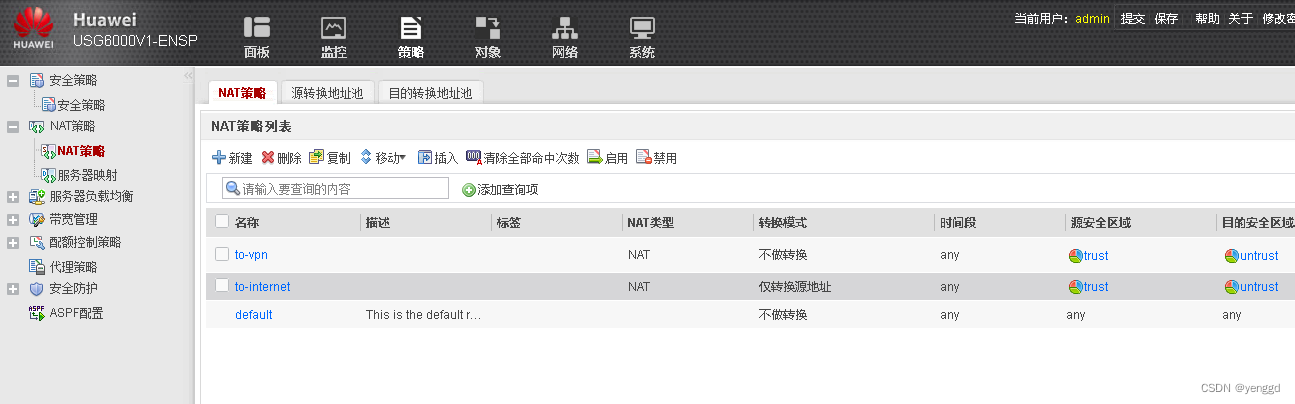
nat配置:
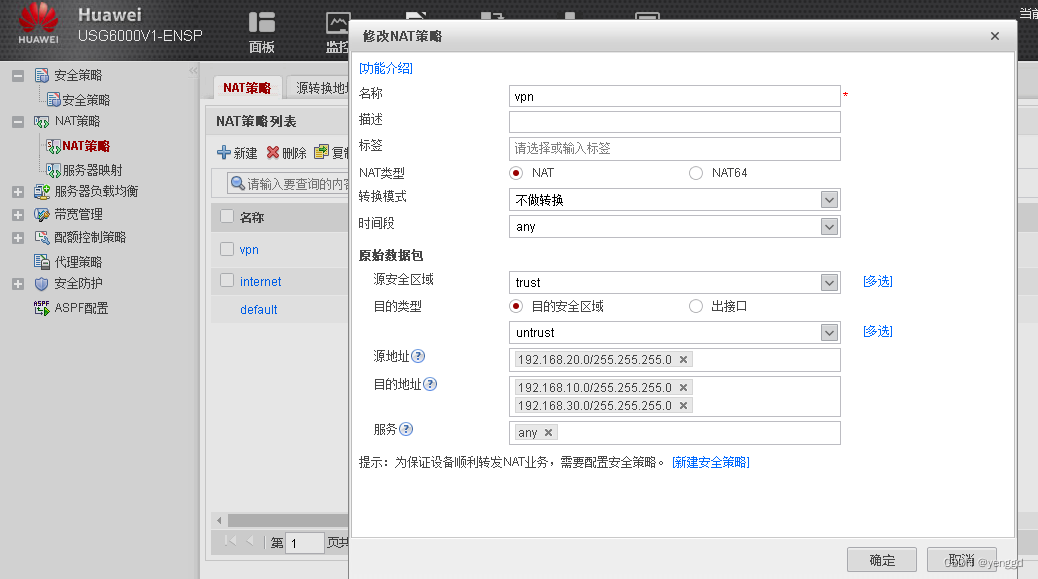
***的不做nat的一定要放上面
去往sz的也得加上去,一共两个网段
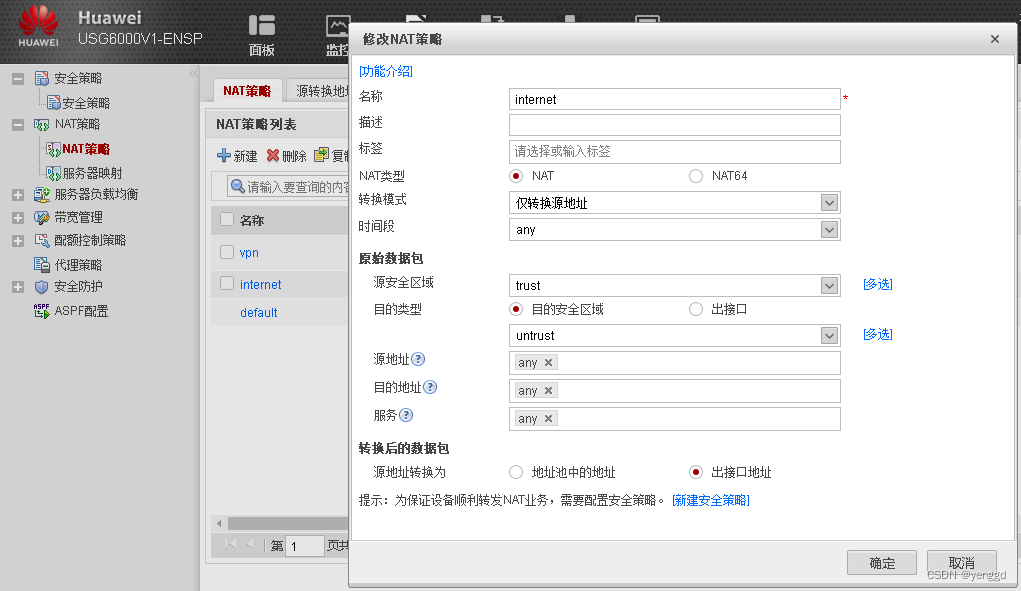
上外网的nat
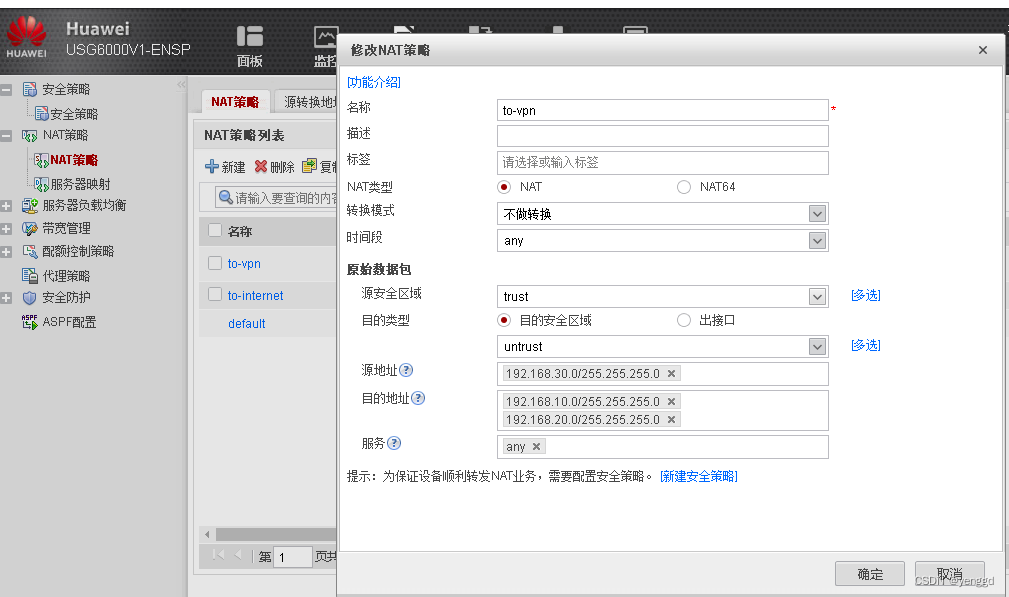
图中***那条策略不做转nat转换,并且放在最上面第一条,上网NAT的放在第二条。
上网nat配置完后成这里会多一条地址不加密的:
FW3配置:
acl number 3000
rule 5 permit ip source 192.168.30.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
rule 10 permit ip source 192.168.30.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
ipsec proposal prop28111041145
encapsulation-mode auto
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike peer ike281110411459
exchange-mode auto
pre-shared-key adminadmin
ike-proposal 1
remote-id-type ip
remote-id 1.1.1.2
local-id 3.3.3.1
dpd type periodic
remote-address 1.1.1.2
ipsec policy ipsec2811104114 1 isakmp
security acl 3000
ike-peer ike281110411459
proposal prop28111041145
tunnel local applied-interface
alias to-bj
sa trigger-mode auto
sa duration traffic-based 10485760
sa duration time-based 3600
interface GigabitEthernet0/0/0
undo shutdown
ip binding ***-instance default
ip address 10.1.1.10 255.255.255.0
alias GE0/METH
service-manage https permit
interface GigabitEthernet1/0/1
undo shutdown
ip address 192.168.30.1 255.255.255.0
service-manage ping permit
dhcp select interface
interface Virtual-if0
interface NULL0
firewall zone local
set priority 100
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
firewall zone dmz
set priority 50
ip route-static 0.0.0.0 0.0.0.0 3.3.3.3
security-policy
default action permit
nat-policy
rule name to-***
source-zone trust
destination-zone untrust
source-address 192.168.30.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
action no-nat
rule name to-internet
source-zone trust
destination-zone untrust
source-address 192.168.30.0 mask 255.255.255.0
action source-nat easy-ip
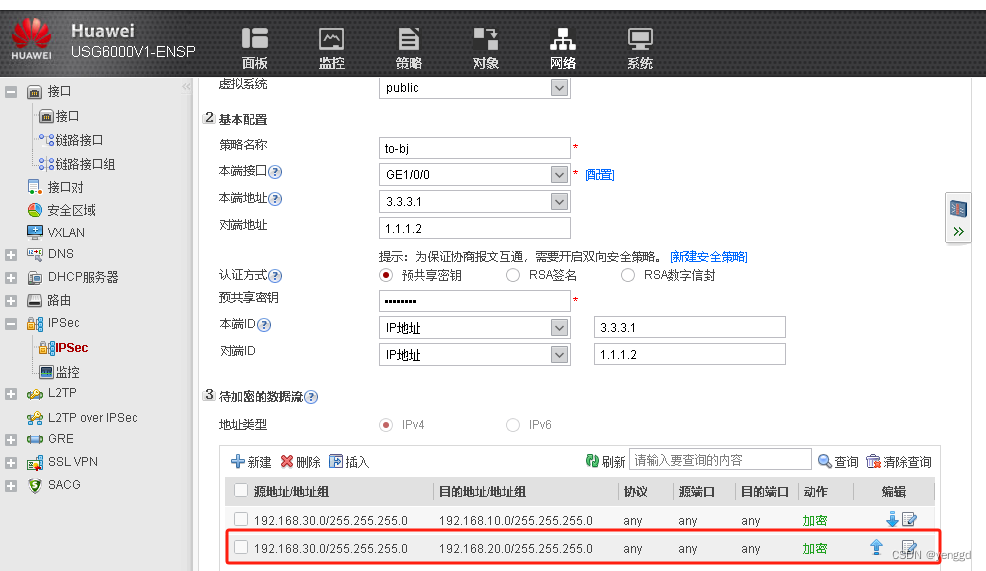
FW3的web配置:
最后一条网段要手动添加上去
NAT配置:
和gz分部配置同样